I participated in WPI 2020 with my team P1rates and I was able to solve some cool challenges with them. This is my writeup about some of them that I managed to solve during the competition.
Stego
1. Luna
They say the full moon makes people go crazy… hopefully this stego won’t have the same effect on you!
This challenge was the most interesting one I solved during the
competition. It gives us an archive
Luna.tar.xz
and it contains a
1.png
image and another password protected archive
so you take the moon.zip.
I tried to extract the password hash to crack it with
john
but it seems it was uncrackable password, so let’s look at the
image.
It’s just an empty white image nothing usefull in it, so let’s
try to run
exiftool
to see any hidden text.
root@kali:~# exiftool 1.png
ExifTool Version Number : 11.93
File Name : 1.png
Directory : .
File Size : 7.4 kB
File Modification Date/Time : 2020:03:21 01:56:12+02:00
File Access Date/Time : 2020:04:20 04:24:50+02:00
File Inode Change Date/Time : 2020:04:20 04:24:50+02:00
File Permissions : rw-rw-r--
File Type : PNG
File Type Extension : png
MIME Type : image/png
Image Width : 300
Image Height : 300
Bit Depth : 8
Color Type : RGB
Compression : Deflate/Inflate
...
Thumbnail Offset : 414
Thumbnail Length : 1651
Time Created : 19:56:12-19:56
XMP Toolkit : XMP Core 4.4.0-Exiv2
Digital Source Type : http://cv.iptc.org/newscodes/digitalsourcetype/softwareImage
Document ID : gimp:docid:gimp:456e1492-77c3-4f45-92c3-edd0541a4413
Instance ID : xmp.iid:3e22a217-d4a0-422b-9bc6-58f60eddf54d
Original Document ID : xmp.did:cc8dad5e-07b5-4920-9533-fc26a32b80f0
Model Release Status : None
Study Physician : awcIsALegendAndIHopeThisIsAStrongPasswordJackTheRipperBegone
Api : 2.0
Platform : Linux
Time Stamp : 1584748572978367
Version : 2.10.18
Format : image/png
Caption Writer : j00t
Date Created : 2020:03:20
Creator Tool : GIMP 2.10
Rating : 5
Person In Image : type="Bag" jutin
History Action : saved, saved, saved, saved, saved
History Changed : /metadata, /, /metadata, /metadata, /
History Instance ID : xmp.iid:967142e5-a3e0-4326-8335-bbe854fe7477, xmp.iid:8b519cd0-a1e9-41f7-ae1b-5b66b66b699e, xmp.iid:b7345da5-469a-491b-86b2-ad14b96f1132, xmp.iid:69b7dcf5-be9f-446d-8614-9ddda3bded58, xmp.iid:f39a3ecb-64e6-4b8b-98f1-fcb5eb4e1539
History Software Agent : Gimp 2.10 (Linux), Gimp 2.10 (Linux), Gimp 2.10 (Linux), Gimp 2.10 (Linux), Gimp 2.10 (Linux)
History When : -04:00, -04:00, -04:00, -04:00, -04:00
...
The image contains some useful info but there is one thing that
made me pay attentionStudy Physician:
awcIsALegendAndIHopeThisIsAStrongPasswordJackTheRipperBegone. So when I tried to unzip the archive with that password it
worked and gave me 2 another files
Just In Case.png
and
jut.
The image wasn’t useful for me maybe there is another solution i
don’t know, but the other file seems interesting. The
file
command didn’t recognize it so let see the magic bytes.
00000000 42 50 53 31 54 42 8F 37 15 90 80 08 80 21 23 80
BPS1TB.7.....!#.
First I assumed that maybe a Photoshop
PSD
file since the magic bytes look similar. However I’ve tried to
add the missing bytes and open it with Photoshop, but the file
looks corrupted. I struggled at this point for some time, so
let’s run
binwalk
to see any hidden files.
root@kali:~# binwalk jut
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
45 0x2D Zlib compressed data, best compression
There is a
zlib
file at position
0x2d
let’s extract it.
root@kali:~# dd if=jut bs=1 skip=45 of=file.zlib
17893+0 records in
17893+0 records out
17893 bytes (18 kB, 17 KiB) copied, 0.0917604 s, 195 kB/s
Now, we have
zlib
compressed file the goal is to extract and see if it contains
any data. I wrote a
bash
line code to take the file and extract the data using
zlib
library in python.
#!/usr/bin/bash
cat $1 | python -c "import zlib,sys;sys.stdout.write(zlib.decompress(sys.stdin.read()))"root@kali:~# ./extract.sh file.zlib
exif
5364
45786966000049492a00080000000a0000010400010000002c0100000101040001000000
2c0100000201030003000000860000001a010500010000008c0000001b01050001000000
94000000280103000100000003000000310102000d0000009c0000003201020014000000
aa0000006987040001000000be0000002588040001000000d00000003201000008000800
0800fc2900005b000000fc2900005b00000047494d5020322e31302e3138000032303230
3a30333a32302031393a30343a313700010001a003000100000001000000000000000300
0200050003000000fa00000004000500030000001201000006000500010000002a010000
000000000000000001000000000000000100000000000000010000000000000001000000
00000000010000000000000001000000000000000a000000080000010400010000000001
000001010400010000000001000002010300030000009801000003010300010000000600
000006010300010000000600000015010300010000000300000001020400010000009e01
000002020400010000005013000000000000080008000800ffd8ffe000104a4649460001
....
a0028a28a0028a28a0028a28a0028a28a0028a28a0028a28a0028a28a0028a28a0028a28
a0028a28a0028a28a0028a28a0028a28a0028a28a0028a28a0028a28a0028a28a00fffd9
It looks interesting some hex bytes and I noticed that the last
2 bytes
ff d9,
so I assumed it’s a
jpg
image I searched for the first magic bytes
ff d8 ff
I found it at line
12 so
let’s put those values into a new hex editor and save it as
flag.jpg.
Thanks to
Jutin
the creator of this challenge. the flag:
WPI{M00N_mOOn}
Crypto
1. Illuminati Confirmed
I’ve intercepted multiple copies of an encrypted message from the leader of the Worcester chapter of the Illuminati. I think it contains the time of their next meeting. Can you help me decrypt them?
c1=515274042976912179894435774656907420040599503456517078488056218986662017260212389975972477279505310799399071383390618892499008790928347543017765027618590150794317674792875250152206518326158674718404382617692169589911938548819188733852354294583496715425255584973283840789780326402769751705164900106921523637157271605500111846563844641773661723255718653040958019618435501230171699432186518803652675691180548548982155426472648502704469425298466513665043628724497448475714424482446137414939511691724839553567514050622159418495196773388690852258256550787962177196383253952227153557220272199293397879908308572668952866439
c2=10512934566887371506285681495672139256544177416158977932082410009242386741198073874632763611137937701329570263046854521709347241390006612379393018933295475369159148328248445221357906382527678877429535168220389698475391828837227453358681276167720605617228338487308750653165147019400915842904872988789759529121710032871148507314874152494680057046977274373381326003405301191489108322498519602528688873942243307708631394538177629868515911161222795303220989599519719169300455717641863368473309673489958952173445661451265442004625237606054046962062434813126456494957846077185121041599277143211160596207640833275850170891378
c3=4122591425712279559823043898131225014447235394996958162806737555257607173149332839353292933732548212376056402900761362427837044396517072345683265668973735260384169928448531246071624967168190024583028639591981238222340513125989229227761894026521238496145716707176637113415430809586007230597253976748507442809040629281971868442704017013258355403718545489677897799000961350863824810217217745918503635905775610161826572608564207497464646323778407843991683950506484189720225535503643332574132841288909783555334280205740975729691459011043954137669831817945210956835398278009161994675851980163314376477384045294293755909874
n1=21939147590581954242131893557689750173730181114330873782062274456630281986233643990882568426690149971468987847436717513764939861105600249325682418749886588739440853385485272501856860578476795830603738468829294920737586209822299603185425324611481798231193950636987017718955070420091525231666894903436050998112803225822333684113551754209802262129292376015861410644289380376439390552627189657966103965089679163295591136464541998227543058082734503570960156783196006833967361311083486266118899788620317372054292861892020849652213277431575285275801196626852675579752895079650118836892859390462805733596279690076656763624249
n2=26325215018784165663958487526715385161171636566916698114816183716597566424675870012796860473421390775180027083457908584461525282815469520282303059318923930531826588673345113634118988713179894971211405380241575065877886390347877768297280022387015195069836149198306647472534681286406136303674462323742151285361538383784282113898065157278366533587767199303585208673225974716800760227497569577072903884939422787710986913747191378087554442395968729847569180921093186599977266346501947184849099856506537976370069200813758143237937721729073822639191799709052936074831322440705620902220824412476988222346922869104007199777561
n3=23013589835547680503802140462487647716102548445081685245087901486321520435018899614072711065158868927754813316329675676910885474767916372370942795565358071859270832973837949423193707764788999822539648518439967218163608118921979697363190728350735745938069012584523314223346479156208977445194408267152808800890485882602068876756801123087623323707553203656108124651989136578687688847505350883163751096338640206246619001851586459510648241545637475283654557530338836698680934504086346810521919864048046078444168117563048636886066060497385368685340990757248020960409380316695810483273153565980791846594355984630591111120973
e=3
The challenge very obvious it gives us some
c1 c2 c3
and
n1 n2 n3
with
e=3 I
know it’s a
RSA
challenge with very famouse
Chinese Remainder Theorem
and
Coppermith Attack.
Now, the goal is to find
M such
that
C = M^3 mod(n1*n2*n3)
and we know that
M < Ni
so
C = M^3
and
M is
our message (flag).
Hopefully, there is a method in
sympy
library to compute
C and
get the flag.
from sympy.ntheory.modular import crt
from sympy import root
c1=515274042976912179894435774656907420040599503456517078488056218986662017260212389975972477279505310799399071383390618892499008790928347543017765027618590150794317674792875250152206518326158674718404382617692169589911938548819188733852354294583496715425255584973283840789780326402769751705164900106921523637157271605500111846563844641773661723255718653040958019618435501230171699432186518803652675691180548548982155426472648502704469425298466513665043628724497448475714424482446137414939511691724839553567514050622159418495196773388690852258256550787962177196383253952227153557220272199293397879908308572668952866439
c2=10512934566887371506285681495672139256544177416158977932082410009242386741198073874632763611137937701329570263046854521709347241390006612379393018933295475369159148328248445221357906382527678877429535168220389698475391828837227453358681276167720605617228338487308750653165147019400915842904872988789759529121710032871148507314874152494680057046977274373381326003405301191489108322498519602528688873942243307708631394538177629868515911161222795303220989599519719169300455717641863368473309673489958952173445661451265442004625237606054046962062434813126456494957846077185121041599277143211160596207640833275850170891378
c3=4122591425712279559823043898131225014447235394996958162806737555257607173149332839353292933732548212376056402900761362427837044396517072345683265668973735260384169928448531246071624967168190024583028639591981238222340513125989229227761894026521238496145716707176637113415430809586007230597253976748507442809040629281971868442704017013258355403718545489677897799000961350863824810217217745918503635905775610161826572608564207497464646323778407843991683950506484189720225535503643332574132841288909783555334280205740975729691459011043954137669831817945210956835398278009161994675851980163314376477384045294293755909874
n1=21939147590581954242131893557689750173730181114330873782062274456630281986233643990882568426690149971468987847436717513764939861105600249325682418749886588739440853385485272501856860578476795830603738468829294920737586209822299603185425324611481798231193950636987017718955070420091525231666894903436050998112803225822333684113551754209802262129292376015861410644289380376439390552627189657966103965089679163295591136464541998227543058082734503570960156783196006833967361311083486266118899788620317372054292861892020849652213277431575285275801196626852675579752895079650118836892859390462805733596279690076656763624249
n2=26325215018784165663958487526715385161171636566916698114816183716597566424675870012796860473421390775180027083457908584461525282815469520282303059318923930531826588673345113634118988713179894971211405380241575065877886390347877768297280022387015195069836149198306647472534681286406136303674462323742151285361538383784282113898065157278366533587767199303585208673225974716800760227497569577072903884939422787710986913747191378087554442395968729847569180921093186599977266346501947184849099856506537976370069200813758143237937721729073822639191799709052936074831322440705620902220824412476988222346922869104007199777561
n3=23013589835547680503802140462487647716102548445081685245087901486321520435018899614072711065158868927754813316329675676910885474767916372370942795565358071859270832973837949423193707764788999822539648518439967218163608118921979697363190728350735745938069012584523314223346479156208977445194408267152808800890485882602068876756801123087623323707553203656108124651989136578687688847505350883163751096338640206246619001851586459510648241545637475283654557530338836698680934504086346810521919864048046078444168117563048636886066060497385368685340990757248020960409380316695810483273153565980791846594355984630591111120973
N = [n1,n2,n3]
C = [c1,c2,c3]
M = crt(N, C)[0]
m = root(M,3)
print m
And I got ascii integer values for the flag:
WPI{Ch1n3s3_R3M@ind3R_Th30r3m_!_}.
Reverse
1. NotWannasigh
Please help! An evil script-kiddie (seriously, this is some bad code) was able to get this ransomware “NotWannasigh” onto one of our computers. The program ran and encrypted our file “flag.gif”. These are the resources we were able to gather for you:
- the malicious ransomware executable
NotWannasigh.zip- our poor encrypted file that we need you to recover
flag-gif.EnCiPhErEd- the note left behind by the ransomware. I’m not sure you’ll find anything usefull here ransomNote.txt
- a packet capture that our IDS isolated, it seems that the program has some weird form of data exfiltration
192-168-1-11_potential-malware.pcap- We need you to reverse the malware and recover our flag.gif file. Good luck! A note from the creator: Shoutout to Demonslay335 for challenge inspiration - he’s done some awesome work in fighting ransomware. Also, the ransomware in this challenge is programmed to only target files named “flag.gif” so you shouldn’t need to worry about the accidental execution, I just zipped it out of habit/good practice. Have fun and happy hacking!
The challenge was a little bit easy for me it gives us some
network traffic
pcap
file, a binary, a text note, and the encrypted flag file. The
goal here is to debug the binary and see what it does and
reverse the process of encryption. Let’s open the binary in
IDA
and see what it looks like.
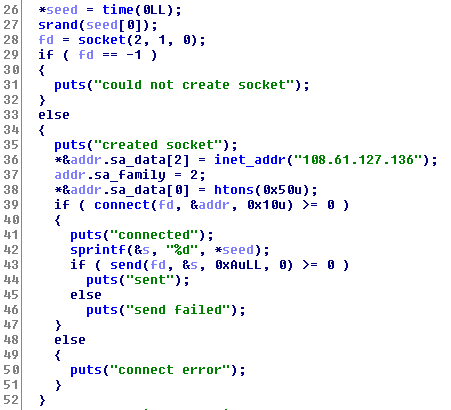
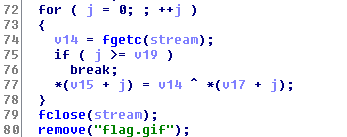
I noticed there is a main function with some heavy code, so
let’s analyze it. From line
26 to
52
it’s just seeds the
srand
with the current time, trying to connect to the socket with
address
108.61.127.136, send the seed value and thats so interesting because the same
seed produce the same random values.
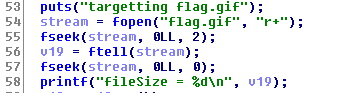
From line
54 to
58 it
opens the
flag.gif
file in the read mode, save the file size at
v19
and print it.
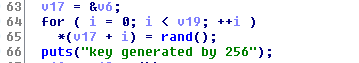
From
63 to
66 it
produces the random values and put them into an integer array
v17 of
the same size of the
flag.gif.
At lines
72 to
80 it
gets the current value from the file, do bitwise
xor
with the current random value of array
v17,
append the result into an array
v15,
close the file, and remove it.
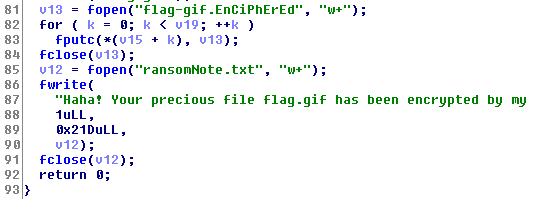
The last lines
81 to
92 it
opens a new file
flag-gif.EnCiPhErEd
in the write mode, put each value of the aray
v15
into the file, close the file, open another file to write the
text note.
Now, let’s see the seed value in the pcap file.
root@kali:~# strings 192-168-1-11_potential-malware.pcap
<n!@
4n"@
>n#@
1585599106
4n$@
d|l=
HHTTP/1.1 400 Bad Request
Server: nginx/1.16.1
Date: Mon, 30 Mar 2020 20:14:58 GMT
Content-Type: text/html
Content-Length: 157
Connection: close
<html>
<head><title>400 Bad Request</title></head>
<body>
<center><h1>400 Bad Request</h1></center>
<hr><center>nginx/1.16.1</center>
</body>
</html>
root@kali:~# date -d @1585599106
Mon 30 Mar 2020 10:11:46 PM EET
I assumed the seed value is
1585599106
and I checked with
date
it tells me the acual time when the program ran.
After that I have the seed and the encrypted flag file, so let’s
wrote some code the reverse the process and get the
file.gif.
#include<stdio.h>
int SEED = 1585599106, SIZE;
void main(int argc, char **argv) {
srand(SEED);
FILE *stream = fopen("flag-gif.EnCiPhErEd","r+");
fseek(stream, 0, 2);
SIZE = ftell(stream);
fseek(stream, 0, 0);
int *keys = (int*) calloc(SIZE, sizeof(int));
char *dec_bts = (char*) calloc(SIZE, sizeof(char));
for(int i = 0; i < SIZE; ++i) keys[i] = rand();
for(int i = 0; i < SIZE; ++i) {
char enc = fgetc(stream);
dec_bts[i] = (char)(enc ^ keys[i]);
}
fclose(stream);
FILE *flag = fopen("flag.gif","w+");
for(int i = 0; i < SIZE; ++i) fputc(dec_bts[i], flag);
fclose(flag);
}
And the flag:
WPI{It_always_feels_a_little_weird_writing_malware}