I participated in AUCTF 2020 with my team P1rates and I was able to solve some cool challenges with them. This is my writeup about some challenges I managed to solve during the competition.
Forensics
1. Block2
The challenge want to get the time when the player of
Mine Craft
rolled back and give us
co_block.sql
file with data inside it. I looked into the file and I saw
rolled_back
column if it is
1 it
rolled back otherwise
0. So,
I wrote
python
script to get the flag.
#!/usr/bin/env python
with open('co_block.sql', 'r') as f:
for line in f.readlines():
line = line.strip().split('\t')
line = [v.strip(',') for v in line]
try:
if line[3] == '1':
print 'auctf{' + line[1] + '}'
break
except:
passThere is another solution to this challenge and that is:
-
Start your
MySQLserverservice mysql startand create a new database. -
Import the given file into the database
mysql -u root -p auctf < co_block.sql. - After that you can select what you need from the database.
root@kali:~# mysql -u root -p auctf -e "SELECT time FROM co_block WHERE rolled_back = 1;"
Enter password:
+------------+
| time |
+------------+
| 1581060905 |
+------------+
The Flag:
auctf{1581060905}
2. Animal Crossing
This challenge gave us a
pcapng
file with a lot of dns traffic after open it with
strings
I saw some weird values sended by
DNS
traffic.
root@kali:~# strings animalcrossing.pcapng | less
quickbrownfoxes
9RGlkIHlvdSBldmVyIGhlYXIgdGhlIHRyYWdlZHkgb2YgRGFydGggUGxhZ
quickbrownfoxes
quickbrownfoxes
9RGlkIHlvdSBldmVyIGhlYXIgdGhlIHRyYWdlZHkgb2YgRGFydGggUGxhZ
quickbrownfoxes
...
quickbrownfoxes
hostmaster
925pYy4gSGUgY291bGQgc2F2ZSBvdGhlcnMgZnJvbSBkZWF0aCwgYnV0IG
quickbrownfoxes
925pYy4gSGUgY291bGQgc2F2ZSBvdGhlcnMgZnJvbSBkZWF0aCwgYnV0IG
quickbrownfoxes
After I extrqacted the distinct values and put them into a file
it looks like
base64
values and after decoding it contains the flag.
The Flag:
auctf{it_was_star_wars_all_along}
3. Boom
The challnege give me
boom.sql.gz
file I tried different approaches to solve this challenge and
extract the hidden file but nothing worked but this one that I’m
going to explain:
-
Run
MySQLserver to create a new database calledauctf. -
Import
boom.sqlfile into the created database. -
Export the hidden archive file into a new one using some
SQLcommand.
Solution:
-
Start
MySQLserverservice mysql start. -
Dump the given file into the database
mysql -u root -p auctf < boom.sql. -
Export the archive with the following
mysql -u root -p auctf -e "SELECT image INTO DUMPFILE '/tmp/flag.7z' FROM images;"
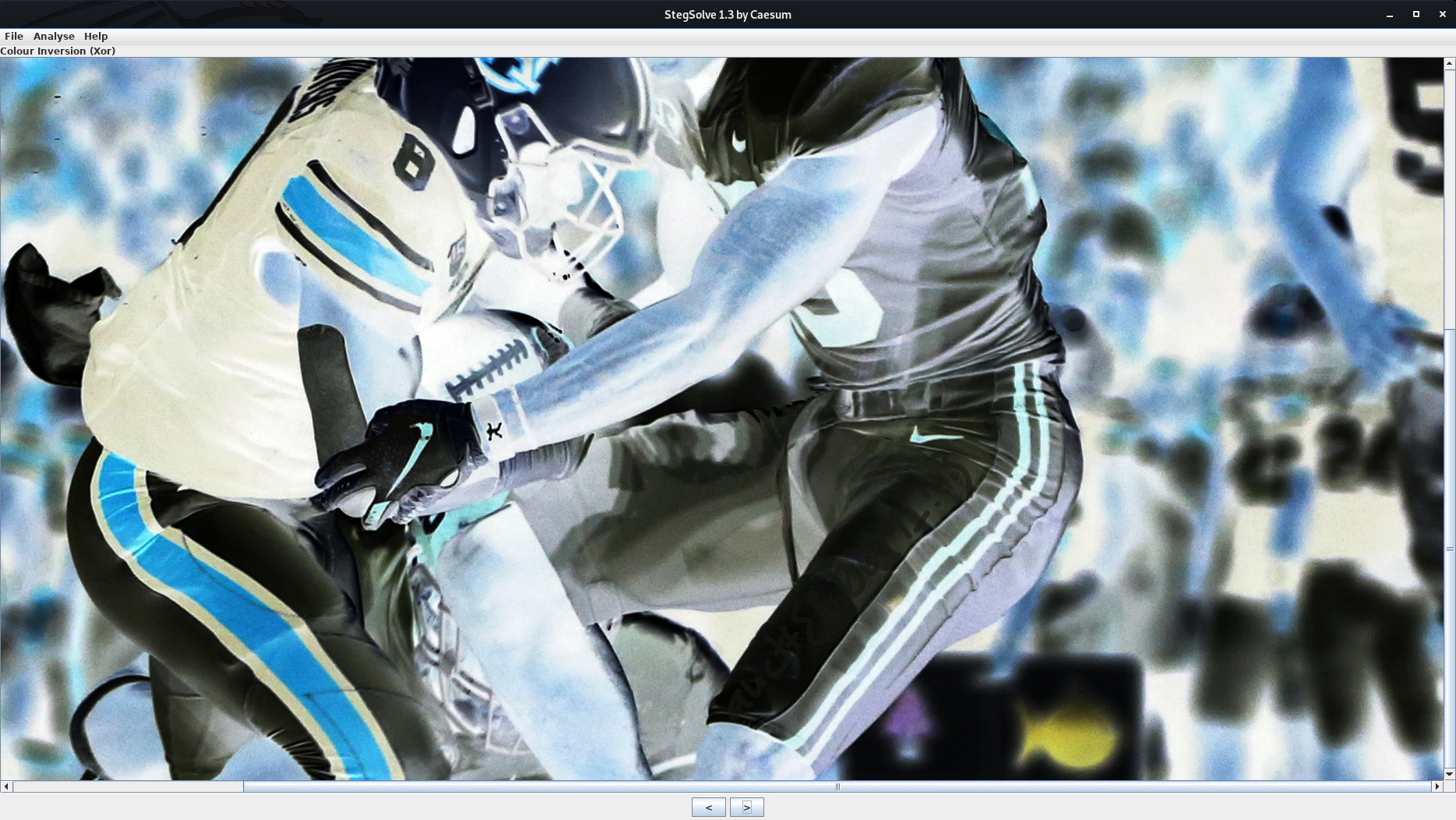
After extracting the archive I got a
PNG
image, I ran
stegsolve
to see any hidden data, and I got the flag at
XOR
channel.
The Flag:
auctf{B00M_!!}
4. Fahrenheit 451
This challenge also gave us
pcapng
file I run strings on it but nothing usefull. I ran
binwalk
I saw
PDF
file at offset
0x25326
and tried to extract it it was corrupted.
root@kali:~# binwalk f451.pcapng
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
152358 0x25326 PDF document, version: "1.5"
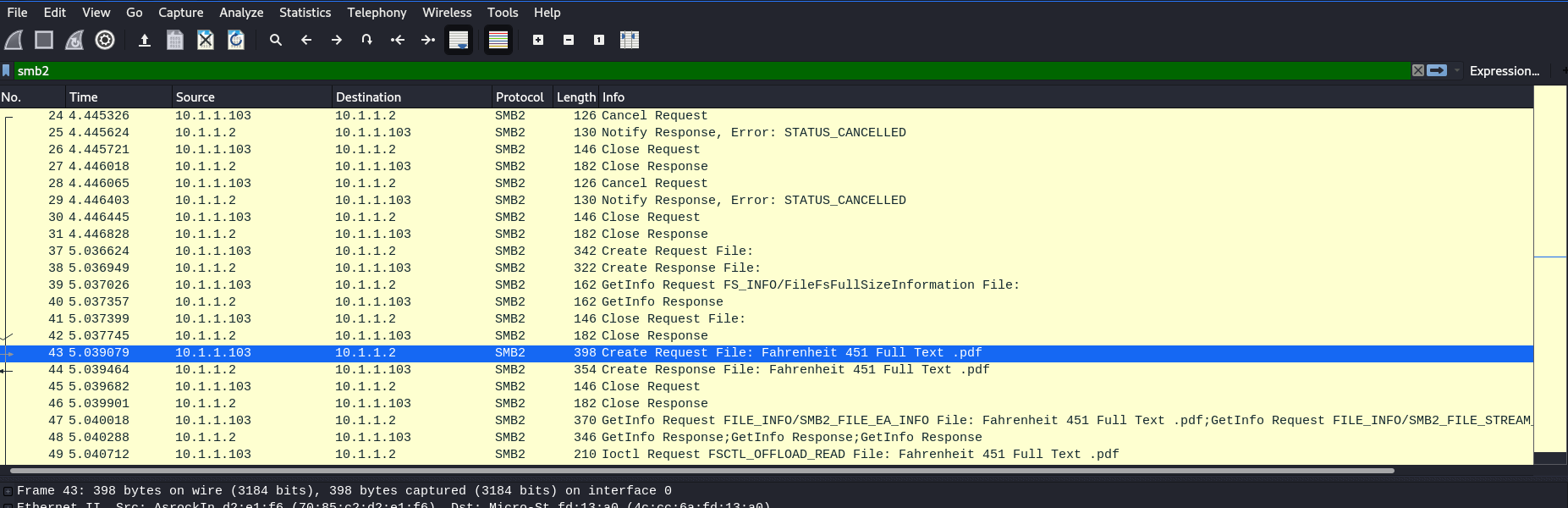
So, I decided to open
wireshark
to get the actual file, I saw some
SMB
traffic and it might be the file is transfered with this
protocol. I exported the objects with
File -> Export Objects -> SMB
I got the
PDF.
I struglled a lot with this file to see how I can do with it and
I assumed that maybe there is some hidden texts inside the
PDF I
opened it and press
CTR + A
to select all text and I saw some hidden weird value at page 7.
It looks like garbage, but he given a word
Substitute
as a hint in the challenge description
2F4E7L3FC?0E9603@@<DPP`PN
so I opened
ascii
table and observe the values with
auctf{. He just subtracted the actual flag with
47, so
I wrote some lines of code to get the actual flag.
#!/usr/bin/env python
cipher = '2F4E7L3FC?0E9603@@<DPP`PN'
flag = ''
for c in cipher:
flag += chr(ord(c) + 47)
It gave me part of the flag and the last
4
bytes are also garbage
auctf{burn_the_books\x7f\x7f\x8f\x7f}. But after analysing the last four bytes he just added it with
47
![]()
P -> ! and ` -> 1
The Flag:
auctf{burn_the_books!!1!}
5. Oops
This challenge was a little easy for me it gave us a virtual
hard disk
debmini.vhdx. I tried to mount it, but it is corrupted, so let’s run
binwalk
to see any files or hidden data and extract any thing inside
that disk.
root@kali:~# binwalk debmini.vhdx -e -D='.*'
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
4194304 0x400000 ISO 9660 Primary Volume,
After extraction I got some system files inside
iso-root
folder I examine the folders but nothing useful, so I ran
strings * | grep -oE "auctf{.*}"
and grep for any flag format and I found it.
The Flag:
auctf{pls_dont_delete_me}
Password Cracking
Note: The process of cracking may take a long time to get the password depends on the
wordlistyou use and your machine hardware.
1. Big Mac
The challenge gave us the salt
thisisasecret
and the hash
5ee9fafd697e40593d66bef8427d40f8beca6921
and after analysing the hash it is
SHA1,
but the challenge called
Big MAC. So, the goal here is to find the correct
MAC
type and put the hash with the salt in the correct format to use
hashcat.
The hash type is
HMAC-SHA1
and the format might look like:
5ee9fafd697e40593d66bef8427d40f8beca6921:thisisasecret
Now, after I ran the
hashcat
it gave me the correct password:
root@kali:~# hashcat -a 0 -m 160 big_mac.txt /usr/share/wordlists/rockyou.txt --show
5ee9fafd697e40593d66bef8427d40f8beca6921:thisisasecret:scarface
The Flag:
scarface
2. Zippy
This challenge gave us
zippy.zip
file and it contains 6 other
zip
file that are protected by some passwords, so the goal is to
extract the hashs for every one and crack it with our friend
john.
root@kali:~# zip2john zippy.zip > hash1
root@kali:~# john -w=/usr/share/wordlists/rockyou.txt hash1
root@kali:~# john --show hash1
zippy.zip/unzipme.zip:8297018229:unzipme.zip:zippy.zip:zippy.zip
1 password hash cracked, 0 leftAfter cracking the first pass I repeat the above process to extract the hashes and crack the other passwords:
8297018229
pugh1948
cobra0
madboy99
racoon211
imverygoooooooooooooooooooooooooooooooooooooooooooooooo
LEFTEYE
Now, we extract all files and got the
flag.txt
file. The Flag:
y0ud1d17#15789
3. Manager
The challenge gave us keepass
manager.kdbx
file and told us the password is all digits, so the goal is to
get the password hash, create a wordlist, crack it, and get the
flag inside that file. I used my friend
john
to extract the hash and format it to using
hashcat.
root@kali:~# keepass2john manager.kdbx | cut -d ":" -f2 > hash
root@kali:~# crunch 3 7 0123456789 > numbers.lst
Crunch will now generate the following amount of data: 87654000 bytes
83 MB
0 GB
0 TB
0 PB
Crunch will now generate the following number of lines: 11111000
Now, I ran the following process on my actual host in order to
make hashcat faster, take advantage of my hardware and utilize
my
GPU to
crack the password. And within 3-5 minutes it cracked the
password.
Note: The following command causes screen to lag and you have to run it and let the machine finish its work.
root@kali:~# hashcat -a 0 -w 3 -m 13400 hash numbers.lst --show
$keepass$*2*60000*0*f31bf71589af9d69d3a9d58b97755405de93aedfbefe244129bb5ac64ed8af41*2f0e592de948bbc65eb9738af2daca231ae54c851ceb1e98f16a69e8f5f48336*8a868c9aedf169c857a8734188bba8eb*8f12fb161ef9e102ef805b84f5ee733c2a645b71099cbf8dab1ed750c58756ee*34fe5cf5eb7991a826a71c3330f88ce9c5ed7cf0e041e4e50a24110d2a69cdd7:157865
After open the file and give it the password
157865
it contains.
The Flag:
y0u4r34r34lh4ck3rn0w#!$1678
Web
1. API madness
This challenge was frustrating to my friends and I looked at it in a different way. I’ll explain my way of thinking in simple words because the challenge is no longer available.
Solution:
-
When I go to the
URLI got some info about the site and gave me/static/helproute to look. -
After I look what it says there are some endpoints to make
POSTrequests./api/loginto login withusernameandpassword,/api/ftp/get_fileto get afilefrom the server, and/api/ftp/dirto get a directory. -
I tried to make
POSTrequest usingPostmanto login withusernameandpasswordit gave me400bad request, so I assumed it accepts data asJSONformat{"username":"username","password":"password"}. - I send the request and It took about 2-3 minutes to finish, so I hold on and after returninig it gave me an error page.
-
I looked at the errors and I saw a stack trace error in the
bottom of the page and the error happened because of some
hidden endpoint
/api/login_checkto check for the token field in the request body. -
Now, I assumed that endpoint is check for the correct
usernameandpasswordand if it’s correct it returns the token. - I tried the above credintials and it worked and gave me the token.
-
Now, I have the token and I know there is
/api/ftp/get_fileendpoint to get a file from the server, so I send the request with following body to get the flag file{"file":"flag.txt","token": "bc842c31a9e54efe320d30d948be61291f3ceee4766e36ab25fa65243cd76e0e"}. -
It returned with the
base64textYXVjdGZ7MHdAc3BfNnJvSzNOX0B1dGh9Cg==and after decode it gives me the flag.
Note: The
/console
page is just a distraction nothing to do with it.
![]()
The Flag:
auctf{0w@sp_6roK3N_@uth}
I’ll update the remaining challenges soon!